Subscribe to our blog.
Subscribe NowSalt Security delivers the industry's only API Posture Governance engine and AI-based Behavioral Threat Protection solution to protect all of your critical APIs.
We have updated and re-designed our Privacy Policy as of March 2024 to make it easier to understand how we collect and use your personal data. Review the new policy.
API are built expressly to share a company’s most valuable data and services. This makes them a lucrative target for bad actors. We’ve already hit the tipping point APIs are now THE way in.
Get the Gartner report“90% of web-enabled applications will have more surface area for attack in the form of exposed APIs rather than the UI.”
Gartner© API Security: What You Need to Do to Protect Your APIs
Salt is the only solution architected specifically to secure modernized, cloud-based app architectures.

Only Salt provides intelligent aggregation and consolidation of your API inventory, with insights into the security posture of your APIs.

Only Salt tracks users over days, weeks, and months to understand, identify, and prevent today’s drawn-out API attacks.

Only Salt leverages insights from bad actors’ minor successes in runtime to craft remediation insights.
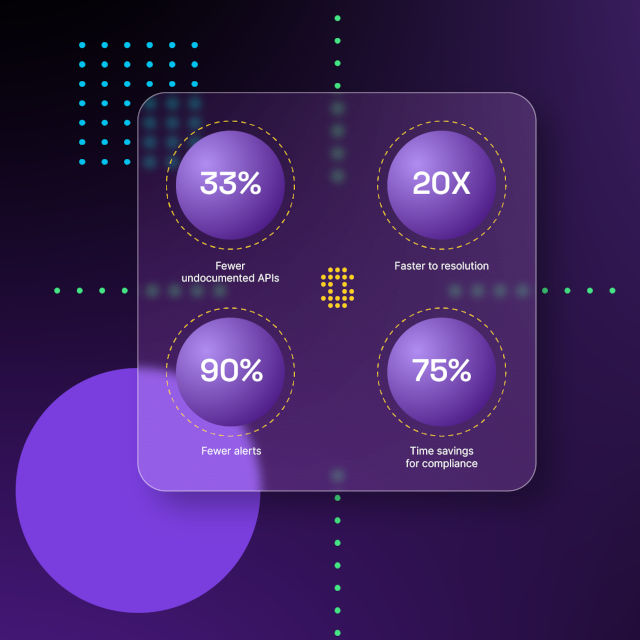
We collect two-way API data, including requests, responses, and numerous behavioral attributes, studying your API activity over extended periods. This data is stored in a versatile data lake, analyzed by AI/ML models to provide you with:

Shield Your APIs from Threats, Hackers, and Vulnerabilities. Download our comprehensive API Security Expert pack for the state of the art security insights.

Case study
Berkshire Bank provides business and consumer banking, mortgage,
wealth management, and investment services.
Case study
Jemena is a leading energy infrastructure company in Australia that operates, manages, and maintains a diverse range of assets across the energy supply chain.

Case study
Xolv's a fully integrated suite of healthcare solutions and quality care outside of the traditional hospital setting.
 Explore all
Explore all
Blog
Hackers could take over millions of accounts on Grammarly, Vidio and Bukalapak. The issue was fixed but users at other websites could still be at risk.
Read the storyBlog
We want to thank our customers, partners and friends for the calls and messages to our team showing your concern and support.

Blog
Salt continues to receive accolades for the Salt Security API Protection Platform – all year round!
 Explore all
Explore all
Resource
APIs fuel today’s digital economy and are a lucrative target for attackers. This eBook explores why API attacks are different and how to protect your organization.
Read the storyResource
The business value of API security.

Resource
Reduce your risk of API attacks while maximizing the value of digital innovation.
 Explore all
Explore allLearn how Salt Security's leading API security platform can provide complete Posture Governance and API Behavioral Threat Protection.

We have updated and re-designed our Privacy Policy as of March 2024 to make it easier to understand how we collect and use your personal data.
Read the new policy